Quzara Blogs
FedRAMP
 |
September 30, 2025 - Quzara's blog, "The Hidden Costs of Ransomware: Beyond the Ransom Note," highlights the often-overlooked financial and operational impacts of ransomware attacks. While the ransom payment is a significant expense, it typically accounts for only a small fraction of the total cost. Additional expenses include downtime, legal fees, regulatory fines, reputational damage, and the implementation of enhanced security measures. The blog also discusses the evolution of ransomware tactics, such as triple-extortion, and the rise of Ransomware-as-a-Service (RaaS) platforms, which have increased the frequency and sophistication of attacks. It emphasizes the importance of proactive cybersecurity strategies to mitigate these hidden costs. |
 |
September 25, 2025 - This guide shows how to plan, run, and review realistic ransomware simulations for red teams and blue teams to expose gaps and improve detection and response. It walks through setting objectives, emulating each stage of the kill chain, running purple team exercises, and capturing metrics like mean time to detect and mean time to recover so you can refine playbooks. |
 |
September 23, 2025 - Quzara's blog on ransomware trends in 2025 highlights the evolving tactics of cybercriminals and offers practical defense strategies. It discusses the rise of triple-extortion schemes, where attackers not only encrypt data but also steal and threaten to release it, and may even launch DDoS attacks. The piece also examines the role of Initial Access Brokers in facilitating attacks by selling credentials and access points, and emphasizes the importance of implementing multi-factor authentication and monitoring for unusual login patterns to mitigate these threats. Additionally, the blog covers the growing sophistication of ransomware-as-a-service operations and provides actionable insights for organizations to bolster their defenses. |
 |
September 18, 2025 - Quzara’s “CMMC Compliance Checklist 2025 Edition” offers a practical, step-by-step guide for defense contractors preparing for the Department of Defense’s updated cybersecurity requirements. The blog breaks down the essentials of CMMC 2.0, including the three certification levels, the shift to NIST 800-171 alignment, and the introduction of self-assessments for certain levels. It emphasizes the importance of thorough documentation, such as System Security Plans and incident response logs, to demonstrate compliance during audits. Additionally, the post highlights the role of Quzara Compliance Advisory in helping organizations navigate these requirements effectively. |
 |
September 16, 2025 - Quzara’s blog, “CMMC Cost Breakdown: Expect Surprises and Budget Wisely,” offers a detailed guide to help organizations plan financially for CMMC 2.0 compliance. It outlines the typical costs associated with each certification level, including documentation, assessments, and remediation efforts. The blog also provides strategies for reducing expenses, such as leveraging open-source tools and partnering with managed service providers. Additionally, it emphasizes the importance of early preparation to avoid unexpected costs and ensure eligibility for Department of Defense contracts. |
 |
September 11, 2025 - Quzara's blog, "Get Ahead with This Comprehensive CMMC Evidence Collection Guide," provides a practical roadmap for organizations preparing for CMMC assessments. It emphasizes the importance of collecting and organizing objective evidence—such as policies, logs, and training records—to demonstrate compliance with security controls. The guide offers actionable tips for aligning evidence with assessment objectives and streamlining the audit process. |
 |
September 9, 2025 - Quzara’s blog, “CMMC Level 2: What It Takes to Pass and Stay Compliant,” outlines the essential steps for defense contractors aiming to meet the Department of Defense’s cybersecurity standards. It emphasizes the importance of aligning with all 110 security practices from NIST SP 800-171 to safeguard Controlled Unclassified Information (CUI). The post provides practical guidance on preparing for assessments, including maintaining comprehensive documentation and establishing robust security policies. Additionally, it discusses common challenges organizations face during the compliance process and offers strategies to overcome them, ensuring sustained compliance and readiness for future assessments. |
 |
September 4, 2025 - Quzara’s blog, “FedRAMP 20X: Modernization in Motion,” provides an in-depth look at the ongoing transformation of the Federal Risk and Authorization Management Program (FedRAMP). The initiative, known as FedRAMP 20X, aims to accelerate the authorization process for Cloud Service Providers (CSPs) while maintaining rigorous security standards. |
 |
September 4, 2025 - Quzara’s blog, “CMMC Continuous Compliance Strategies,” explains how organizations can maintain cybersecurity practices after initial certification. It covers continuous monitoring, regular vulnerability scanning, and patch management. The post emphasizes keeping policies and controls up-to-date to stay compliant and secure. |
 |
September 4, 2025 - Quzara’s blog, “Continuous Ransomware Monitoring: Why MDR Beats Legacy Defenses,” highlights the limitations of traditional antivirus and SIEM systems in detecting modern, fileless ransomware attacks. It emphasizes the advantages of Managed Detection and Response (MDR) services, which offer 24/7 monitoring, integrated threat intelligence, and automated response to swiftly identify and mitigate threats. The post advocates for a comprehensive security approach that combines advanced analytics, full-fidelity telemetry, and expert-driven incident response to effectively combat evolving ransomware tactics. |
 |
September 4, 2025 - Quzara’s blog, “Ransomware and Regulatory Compliance: Why Agencies and Contractors Must Prepare,” emphasizes the increasing need for federal contractors to demonstrate ransomware resilience to meet compliance standards. It outlines how frameworks like CMMC Level 2, FedRAMP, and NIST 800-171 require organizations to provide evidence of incident response plans, continuous monitoring, and timely reporting. The post offers practical guidance on aligning security practices with compliance requirements to avoid audit failures and potential penalties. |
 |
September 4, 2025 - Quzara’s blog, “Ransomware Readiness Checklist 2025 Edition,” provides a step-by-step guide for organizations to prepare for ransomware attacks. It covers monitoring the attack surface, access controls, detection, response, and recovery. The post emphasizes proactive measures and continuous improvement to reduce risk. |
 |
September 4, 2025 - Quzara's blog on FedRAMP Authorization to Operate (ATO) and Impact Levels provides a comprehensive overview of the FedRAMP program, emphasizing the importance of understanding the three designated impact levels—Low, Moderate, and High. These levels are determined based on the potential adverse effects on federal operations, assets, or individuals if information is compromised. The blog outlines the process of obtaining an ATO, which is essential for cloud service providers (CSPs) aiming to offer services to U.S. federal agencies. It also discusses the significance of selecting the appropriate impact level to align with the sensitivity of the data handled, ensuring compliance and enhancing security posture. |
 |
September 2, 2025 - Quzara’s blog, “CMMC Incident Response Plan: Best Practices for 2025,” explains how organizations can create an effective incident response plan to meet CMMC requirements. It covers defining roles, using monitoring tools, and conducting training and drills. The post also highlights post-incident recovery and lessons learned to improve future responses. |
 |
June 25, 2025 - FedRAMP 20x modernizes cloud security with Key Security Indicators (KSIs) for real-time, automated compliance and improved risk management. It streamlines authorization and reduces documentation for cloud providers and federal agencies. |
 |
June 24, 2025 - Continuous monitoring was weak because it relied on infrequent assessments, causing delays and gaps in security. FedRAMP 20x updates this with real-time monitoring, automation, and key security indicators for faster, proactive compliance and threat response. |
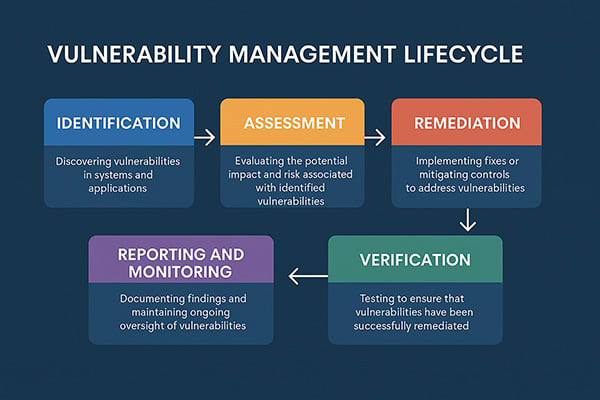 |
June 9, 2025 - The blog outlines a structured vulnerability management lifecycle essential for organizations aiming to meet compliance standards like FedRAMP, CMMC, and FISMA. It emphasizes a continuous, iterative process involving identification, assessment, remediation, verification, and reporting, ensuring robust cybersecurity practices and adherence to regulatory requirements. |
 |
MAY 20, 2025 - "Incident response plays a pivotal role in safeguarding organizations from cyber threats. As cyber attacks become increasingly sophisticated, the need for a structured approach to incident handling is more vital than ever. Effective incident response can..." |
 |
MAY 15, 2025 - "For defense contractors working with the Department of Defense (DoD), cybersecurity isn’t just a priority—it’s a mandate. With the ever-evolving threat landscape, the need for robust cyber incident reporting cannot be overstated..." |
 |
MAY 13, 2025 - "Defense contractors face a unique and formidable challenge: protecting sensitive data while navigating complex regulatory landscapes. Security Operations Centers (SOCs) serve as the frontline defense, ensuring that contractors comply with critical..." |
 |
MAY 8, 2025 - "As TechNet 2025 comes to a close, we’re reflecting on an incredible three-day journey filled with energy, inspiration, and meaningful connections. Our team had the pleasure of engaging with defense leaders, cybersecurity professionals, and government..." |
 |
MAY 7, 2025 - "As the cybersecurity landscape for federal contractors continues to evolve, CMMC Day 2025 arrived at the perfect time — bringing together leaders from across government, industry, and cybersecurity to discuss what’s next for the Cybersecurity Maturity..." |
 |
MAY 1, 2025 - "SOAR, or Security Orchestration, Automation, and Response, is a vital component within Microsoft Sentinel. It enhances the capabilities of Security Operations Centers (SOCs) by automating routine tasks, orchestrating workflows, and providing efficient..." |
 |
APR 29, 2025 - "Threat detection rules are predefined logic sets used to identify potential security threats within an organization's network. These rules analyze various data inputs, searching for anomalous activities that might indicate malicious behavior or policy..." |
 |
APR 24, 2025 - "Cybersecurity has become a critical concern for organizations of all sizes. Microsoft Sentinel has emerged as a leading solution in the realm of cyber defense, offering a comprehensive suite of tools designed to detect, prevent, and respond to..." |
 |
APR 22, 2025 - "In today's cybersecurity landscape, threats are evolving at an unprecedented rate. Traditional incident response methods are no longer sufficient to effectively counter these advanced threats. Cybersecurity professionals must now adopt a modern approach..." |
 |
APR 17, 2025 - "The Cybersecurity Maturity Model Certification (CMMC) is a framework that enhances the cybersecurity posture of companies within the Defense Industrial Base (DIB). Adopting a Zero Trust architecture is essential for meeting CMMC compliance. Zero Trust..." |
 |
MAR 8, 2024 - "Cloud providers aiming to score federal contracts need to unlock the secrets of FedRAMP Gap Assessments. This blog dives into this essential security evaluation, showing how it jumpstarts your journey to FedRAMP compliance and keeps your cloud fortress secure for federal partnerships..." |
 |
MAR 8, 2024 - "This blog post dives deep into FedRAMP, a program that sets security standards for cloud services used by the government. It explains why FedRAMP is important, the different authorization levels, and the steps to achieve compliance. Whether you're a cloud service provider or a government agency, this guide will help you navigate the complexities of FedRAMP.s..." |
|
|
|
 |
FEB 22, 2024- "This blog post is a beginner’s one-stop guide to understanding FedRAMP, a government program that sets security standards for cloud services used by federal agencies. It explains why FedRAMP is important, the different roles involved, and the steps to achieve FedRAMP authorization. If you're a cloud service provider aiming to work with the government, this post offers valuable insights into navigating the FedRAMP process.." |
|
|
|
 |
FEB 29, 2024 - "This blog post explores how Microsoft Sentinel and Defender XDR can empower large organizations managing multiple tenants to enhance their security posture. It dives into the functionalities of each tool, architectural considerations for multi-tenant deployments, and the benefits of using them together, including real-world examples from Quzara Cybertorchs..." |
|
|
|
|
|
|
 |
Infographic - "This infographic provides a clear roadmap to achieving a FedRAMP Moderate compliance level, outlining the actions your organization should take and what to expect at each point along the journey..." |
|
|
|
 |
MAR 15, 2023 - "Cyber security is on everyone’s minds these days, and for good reason. As the number of data breaches and cyber-attacks continues to rise, organizations must take proactive steps to protect their networks and data from malicious actors. One of the best ways to do this is through FedRAMP authorization..." |
|
|
|
 |
FEB 15, 2023 - "Have you ever wondered what goes into achieving FedRAMP compliance? While the process can involve a lot of paperwork and be quite costly, it's important to know that the security measures implemented by FedRAMP are necessary for protecting your company’s cloud assets..." |
|
|
|
|
JAN 23, 2023 - "Digital experiences are at the center of most services that citizens utilize day-to-day, and throughout government they can impact access to important services, such as healthcare, food aid, and housing..." |
Cybertorch
̽����Ƶ
 |
June 24, 2025 - The blog explains that unified SOCs improve cybersecurity by integrating tools, processes, and teams for faster threat detection and response. Fragmented SOCs, with disconnected systems, face inefficiencies and higher risks. |
|
|
|
 |
June 24, 2025 - The blog explains that Risk-Based SOC Optimization helps reduce alert overload by prioritizing high-impact threats aligned with business risks. This approach improves threat detection, speeds response, and enhances team collaboration. |
|
|
|
 |
June 24, 2025 - The blog highlights the importance of securing APIs to prevent breaches and disruptions, focusing on identifying and fixing vulnerabilities throughout development. It recommends automated scanning, strong authentication, encryption, continuous monitoring, and regular security testing as key best practices. |
|
|
|
 |
June 24, 2025 - The blog discusses how integrating Security Information and Event Management (SIEM) tools, like Microsoft Sentinel, can streamline cybersecurity compliance efforts. By automating tasks such as reporting, monitoring, and alerting, organizations can reduce manual workloads and enhance their ability to meet regulatory requirements. The use of artificial intelligence within these tools further aids in proactively identifying and addressing compliance gaps. |
|
|
|
 |
June 19, 2025 - The blog highlights the importance of integrating vulnerability management early in the software development lifecycle through a "shift left" approach, embedding security into CI/CD pipelines to proactively identify and remediate vulnerabilities. It emphasizes the use of tools like Static Application Security Testing (SAST), Software Composition Analysis (SCA), Dynamic Application Security Testing (DAST), and container scanning to enhance security without compromising development speed. |
|
|
|
 |
June 17, 2025 - The importance of SBOMs in vulnerability management is significant. They facilitate proactive identification and remediation of vulnerabilities, enabling organizations to respond swiftly to emerging threats. SBOMs also support compliance with federal and Department of Defense (DoD) requirements, ensuring that software products meet necessary security standards. |
|
|
|
 |
June 11, 2025 - The blog discusses how AI agents integrated into Microsoft Sentinel enhance Security Operations Centers (SOCs) by automating tasks such as threat detection, incident response, and data analysis. These AI agents assist security analysts in identifying and mitigating cyber threats more efficiently, thereby improving overall security posture. |
|
|
|
 |
June 9, 2025 - The blog explains that traditional CVSS scoring is increasingly insufficient for effective vulnerability management because it’s static, inconsistent, and lacks real-world context. It promotes an AI-driven approach—leveraging machine learning, exploit prediction, threat intelligence, and real-time monitoring—to prioritize and remediate vulnerabilities based on actual risk. |
|
|
|
 |
June 3, 2025 - The blog illustrates how Microsoft Sentinel, infused with AI and deep learning, transforms SOCs by enabling automated remediation of low-risk threats, generating contextual executive reports, and aggregating cross-system threat intelligence for proactive defense. It also underscores that in regulated environments, successful deployment hinges on explainable AI, human-in-the-loop oversight with role-based access, and rigorous alignment with compliance frameworks like FedRAMP, CMMC, and FISMA. |
|
|
|
 |
June 3, 2025 - The blog provides a comprehensive, step-by-step walkthrough for installing Microsoft Sentinel, covering everything from preparing your Azure environment and enabling Sentinel on a Log Analytics workspace to connecting data sources and verifying data ingestion. It also offers best practices for configuring analytics rules, automated response playbooks, threat hunting capabilities, real-time dashboards, and cost‑optimization strategies to maintain a scalable and compliant security monitoring solution. |
|
|
|
 |
May 29, 2025 - "The establishment of a Security Operations Center (SOC) is essential for organizations aiming to achieve CMMC Level 2 compliance. This section explores the critical importance of a SOC in meeting the stringent requirements of the Cybersecurity Maturity Model Certification (CMMC) Level 2, which is pivotal for entities operating within the defense industrial base." |
|
|
|
 |
May 27, 2025 - "The establishment of a Security Operations Center (SOC) is essential for organizations aiming to achieve CMMC Level 2 compliance. This section explores the critical importance of a SOC in meeting the stringent requirements of the Cybersecurity Maturity Model Certification (CMMC) Level 2, which is pivotal for entities operating within the defense industrial base." |
|
|
|
 |
May 22, 2025 - "The blog emphasizes that effective Microsoft Sentinel architecture requires strategic planning to align with security and compliance objectives, manage data ingestion costs, and ensure scalability and integration across diverse data sources. It also highlights the value of partnering with experts to optimize analytics rules, automation playbooks, and cost management for a resilient, efficient security monitoring infrastructure." |
|
|
|
 |
Jan 22, 2024 - Quzara, a leading cybersecurity firm specializing in Managed Detection & Response (MDR) and Compliance Advisory services, has proudly joined the Schellman Alliance Program. This strategic alliance between Quzara and Schellman, a topy..." |
|
|
|
 |
JUNE 1, 2023 - "The broad and ever-increasing adoption of digital technology for vital government, public, and private operations has given rise to a parallel, often sophisticated, and constantly evolving, exploitative culture composed of nation-state sponsored and transnational Advanced Persistent Threats (APT), cybercriminals, and hacktivist groups..." |
 |
MAR 23, 2023 - "Security Monitoring and Incident Response are two critical components for any business to enable their data and networks are secure. In this blogpost we will look at the specific requirements mandated by NIST SP 800-171 and CMMC Level 2, as well as take a closer look at why it's important to adhere to these standards and what steps need to be taken to get compliant..." |
|
FEB 9, 2023 - "Splunk vs Microsoft Sentinel: A comparative study will help you understand the key differences between these two tools..." |
|
|
|
|
 |
JAN 31, 2023 - "Microsoft Sentinel is a proactive approach to minimize the risk of a cyber attack that could compromise your organization’s sensitive information..." |
|
|
|
 |
SEP 13, 2022 - "It has become critical for companies to work towards identifying the vulnerabilities that exist in their operational technology (OT). To do that, companies must first know what OT refers to and entails..." |

