Secure. Invisible. Zero Trust Networking at the Edge.
Byos introduces Secure Edge™ hardware-enforced microsegmentation—protecting endpoints and physically isolating them from the local network and providing traffic route enforcement—providing secure connectivity for OT, IoT and IT devices as well as legacy infrastructure. With Byos, endpoints connect over the network, not to it, enabling true device invisibility and eliminating unauthorized discovery, lateral movement, and Wi‑Fi-based threats.
Why Byos Stands Out
- Eliminates Attack Surfaces: Invisible on the network—it’s like your endpoint isn’t even there to attackers
- Microsegmented Protection by Default: Enforces strict policy on device communication and access, even across untrusted networks
- Zero Trust, Simply Delivered: Works with existing hardware, cloud environments, VMs, IoT, and legacy devices—no network redesign needed
Key Capabilities

OS-Independent Security: Byos provides agentless protection, operating independently of the OS, protecting against bypass and stealth attacks targeting the OS— and making Byos immune to host malware.
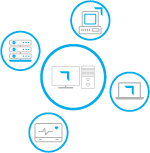
Asset Isolation and Reduced Attack Surface: Each device has an isolated microsegment, keeping assets invisible on local networks and preventing discovery, fingerprinting, and unauthorized access.
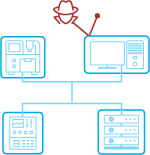
Protection Against Advanced Threats: Enforce Zero Trust principles with least-privilege access, defending against ransomware, spoofing, DoS, and man-in-the-middle attacks.
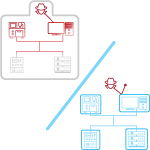
Eliminating Lateral Movement Exposure: Byos eliminates exposure of networked devices to internal threats like lateral movement and ransomware. Even if an intrusion occurs, the ability to limit lateral movement minimizes the potential impact and spread of any breach.
Enhanced Control and Visibility: Gain centralized fleet-wide visibility and threat management of networking assets, and seamless provisioning and access control to any endpoint connected to Byos, regardless of the network.
Ideal Use Cases
- Remote workforce protection on untrusted Wi‑Fi (e.g. home office, cafes, airports)
- Government Agency deployments via federal, state, or local procurement vehicles such as GSA, SEWP, DIRs, etc.
- Organizations needing to enforce Zero Trust in OT and legacy environments without rip‑and‑replace migrations or downtime
To learn more about how Byos' hardware-enforced microsegmentation protects mission-critical networks, visit .