̽����Ƶ, in conjunction with its vendor partners, sponsors hundreds of events each year, ranging from webcasts and tradeshows to executive roundtables and technology forums.
Government Events and Resources
Events

Building Resiliency Across Your Endpoints
Hosted By: Absolute Security & Forescout & ̽����Ƶ
Ransomware attacks often go undetected for months or even years, with attackers escalating privileges before striking. This makes real-time endpoint visibility more crucial than ever, especially in today’s work-from-anywhere environment.
Absolute Security and Forescout discussed how their partnership can help you stay ahead of threats. Together, they offer a powerful solution: the Absolute Connector for Forescout eyeSight, which integrates endpoint visibility with network monitoring and enforcement.
With C2C, Absolute’s endpoint telemetry is integrated with Forescout’s network access control, enabling remediation actions for noncompliant devices, even when off-network.
Attendees learned:
- How to adopt C2C policies that discover and categorize every connecting device, run them through inspection layers and assess them against security benchmarks.
- How to execute manual or automated remediation actions, including sending custom messages or freezing devices when necessary.
- How to continuously monitor device attributes, such as geolocation, as well as security controls like Anti-Malware, Encryption and VPN, ensuring compliance even when off network.
By 2031, ransomware is expected to cost agencies $265 billion annually, with an attack every 2 seconds—unless organizations can effectively monitor users and endpoints, enforce patches and control access.
Fill out the form below to view this archived event.
Resources
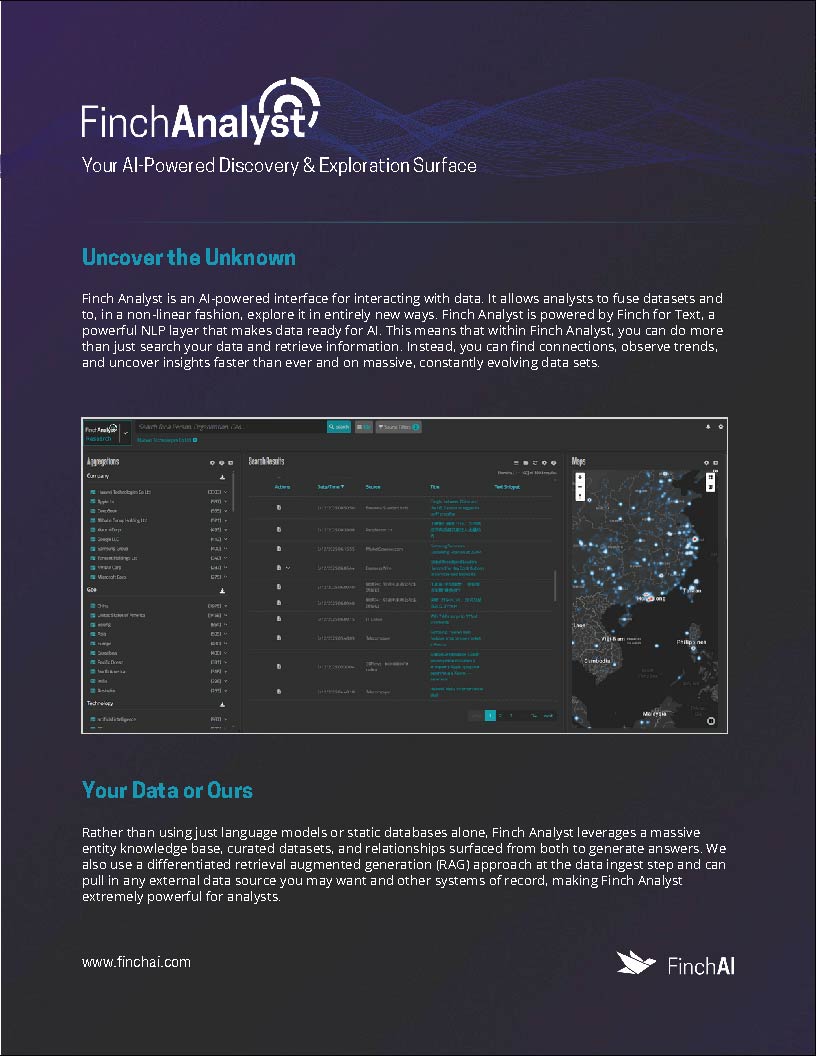
Finch Analyst
Analysts struggle with fragmented data and hidden insights, slowing decision-making and discovery. The Finch Analyst AI-powered platform transforms data interaction by fusing datasets, uncovering relationships, and enabling non-linear exploration. In this solution brief, see how tools like Graph Search, Deep Research, and Risk Assessment agents help analysts surface connections, track trends, and generate intelligence faster and more accurately.
Fill out the form below to view this Resource.
