Explore Forcepoint's Self-Guided Tours
Forcepoint and ̽����Ƶ have partnered together to provide a series of self-guided tours of Forcepoint's products and features. Similar to a live demo, the self-guided tours explores how Forcepoint's products and features applies to a specific technology vertical such as Cybersecurity and Zero Trust.
Learn about Forcepoint's benefits, watch a short pre-recorded demo video, and download related resources. If interested in furthering the conversation, you can also schedule a live demo with a Forcepoint expert from ̽����Ƶ. Start a Self-Guided Tour now by selecting one below:
Forcepoint is committed to protecting Government agencies while facilitating their digital evolution and expansion. Forcepoint’s cutting-edge solutions dynamically adapt to the nuances of human interaction with data, ensuring secure access across various platforms and empowering employees to innovate and drive value. With Forcepoint, data security becomes ubiquitous, fostering productivity and innovation regardless of location. Through our comprehensive suite of solutions, including Forcepoint ONE, agencies can confidently secure access to web, cloud and private applications, while maintaining continuous control over their valuable data assets.
Want to learn more about Forcepoint?
Start a self-guided demo now to learn more about Forcepoint’s proactive cybersecurity solutions.
Forcepoint’s Benefits Snapshot:
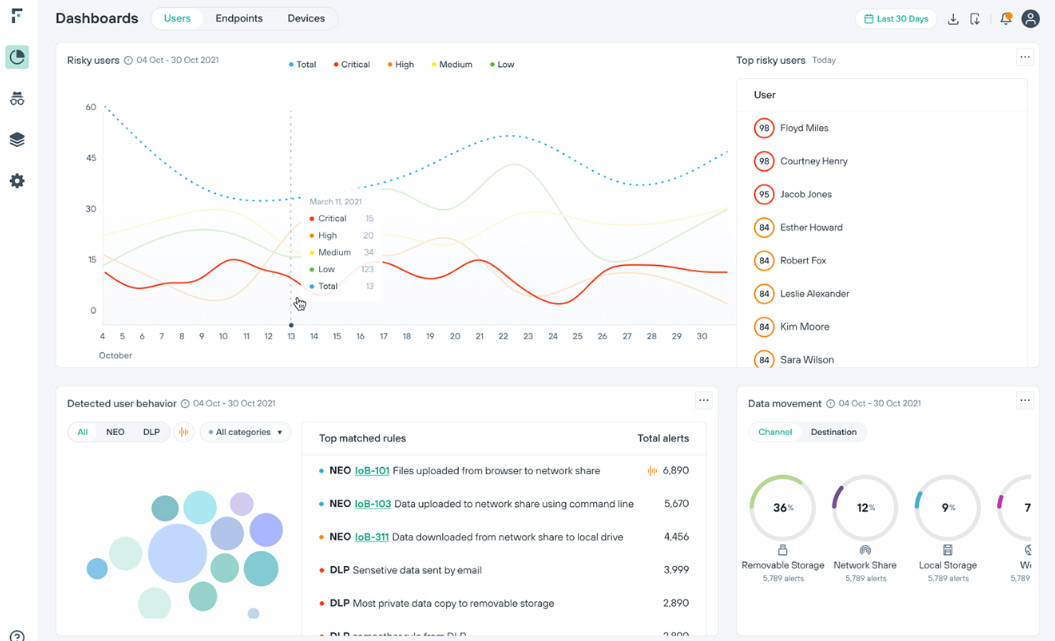
- Utilize data-centric security measures to identify unique behavioral patterns, enhancing threat detection and mitigation strategies.
- Leverage converged capabilities to safeguard your digital ecosystem seamlessly, ensuring holistic security from endpoints to cloud environments.
- Employ advanced AI and data science techniques to uncover valuable insights, utilizing machine learning and analytics for comprehensive behavioral understanding and proactive threat management.
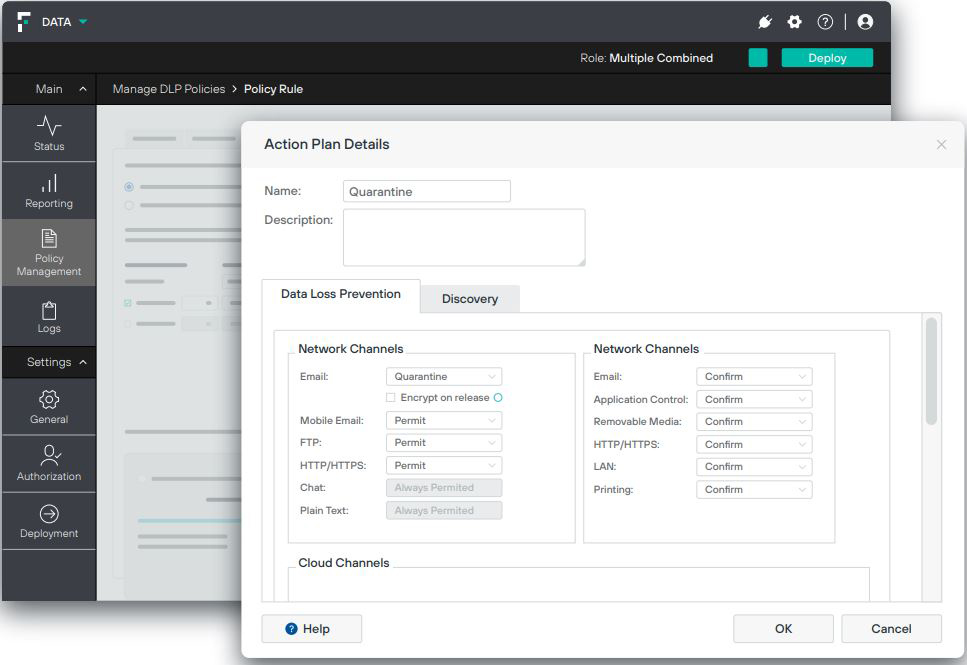
Forcepoint is a leading cybersecurity company focused on empowering Government agencies with advanced Zero Trust solutions through its Forcepoint ONE cloud platform. At the core of this platform is Forcepoint ONE Zero Trust Network Access (ZTNA), a foundational gateway that revolutionizes access control to private web-based applications without relying on traditional VPNs. ZTNA not only enhances security by preventing threats from traversing within networks but also incorporates data loss prevention (DLP) and malware protection for safeguarding critical applications.
Forcepoint’s Zero Trust approach replaces implicit trust with explicit permission, ensuring continuous verification of users, devices and connections based on dynamic criteria such as identity, location and behavior. This proactive security model enables agencies to segment networks, applications and data effectively, minimizing exposure to attacks and providing comprehensive data usage control beyond basic access management. By continuously monitoring the network and employing continuous verification, Forcepoint’s Zero Trust solutions prioritize least-privilege access, granting only essential resources based on specific work requirements and timing, thus significantly reducing the risk of breaches.
Want to learn more about Forcepoint?
Start a self-guided demo now to learn more about cloud security, user verification and Zero Trust solutions.
Benefits Snapshot:
- Enhanced Security: Strengthen security posture by continuously verifying user identities and behavior, ensuring that only authorized users gain access to specific resources, thereby minimizing the risk of unauthorized data access or infrastructure compromise.
- Simplified Access Control: By practicing least-privilege access, Forcepoint reduces the attack surface and limits the impact of breaches, granting access only to necessary resources for specific tasks, bolstering overall security and data protection.
- Comprehensive Data Protection: Unify data security policies across diverse environments, including cloud workloads and SaaS applications, empowering IT teams to dynamically revoke data transfer rights based on users’ actions, ensuring robust data protection and compliance.